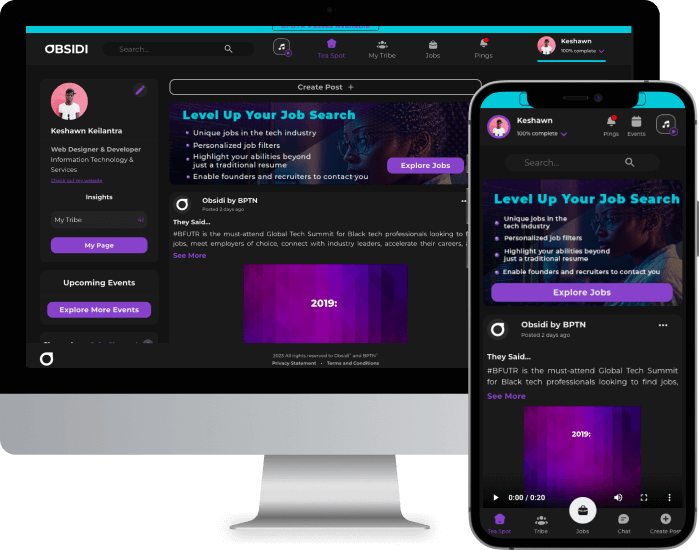















































Thousands of jobs at your fingertips, from employers of choice looking for Black tech talent
BFUTR Global Tech Summit, Obsidi® Academy, Obsidi® Awards, Obsidi® Tech Talks, and other recruitment & networking experiences.
Build a powerful network of tech professionals and executives to level up your career.
Hosted By BPTN
Hosted By BPTN
Presented By BMO
Presented By TD
 Tony Santana
Diversity and Inclusion Consultant - Dell Technologies
Tony Santana
Diversity and Inclusion Consultant - Dell Technologies
"This platform speaks black, talks black, looks out for BLACK, provides master series, mentors, allows you to mentor, you can build communities and then organically connect your communities to other communities and the best part is the best is yet to come."
 Serge Ngatta
Sr. Manager, Product Management - Equifax
Serge Ngatta
Sr. Manager, Product Management - Equifax
"There’s a new professional platform by Black Professionals in Tech Network ( BPTN) Inc. called, Obsidi®. I encourage you to all join and enjoy a network full of opportunities.”
 Siphu Langeni
Data Scientist - Shopify
Siphu Langeni
Data Scientist - Shopify
“In the last week, I’ve had some of the most invigorating convos I’ve had in a while from connections made on the this platform. Thanks BPTN for the insight and the foresight to see the importance of a platform like this! Keep the connections and convos coming!”
